As of Suricata 2.1beta1 - Suricata IDS/IPS provides the availability of packet data and information in a standard JSON output logging capability supplementing further the alert logging output.
This guide makes use of Suricata and ELK - Elasticsearch, Logstash, Kibana.
You can install all of them following the guide HERE
...or you can download and try out SELKS and use directly.
After everything is in place, we need to open the suricata.yaml and make the following editions in the eve.json section:
# "United" event log in JSON format
- eve-log:
enabled: yes
type: file #file|syslog|unix_dgram|unix_stream
filename: eve.json
# the following are valid when type: syslog above
#identity: "suricata"
#facility: local5
#level: Info ## possible levels: Emergency, Alert, Critical,
## Error, Warning, Notice, Info, Debug
types:
- alert:
payload: yes # enable dumping payload in Base64
payload-printable: yes # enable dumping payload in printable (lossy) format
packet: yes # enable dumping of packet (without stream segments)
http: yes # enable dumping of http fields
You can start Suricata and let it inspect traffic for some time in order to generate alert log data.
Then navigate to your Kibana web interface, find an alert record/log and you could see the usefulness of the extra data yourself.
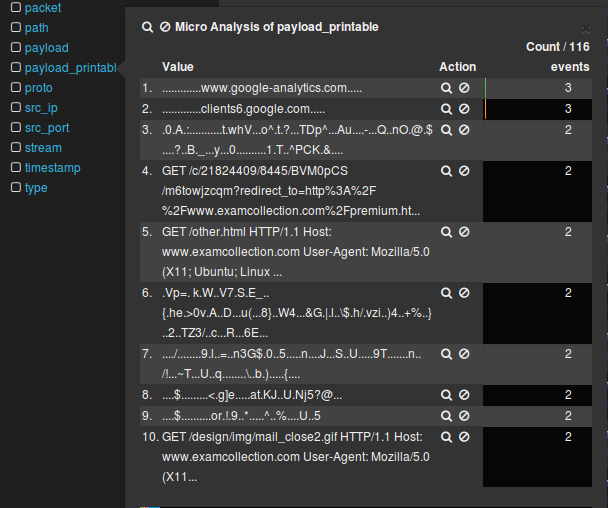
Some examples though :) :
Lets kick it up notch.....
We want to search through -
- all the generated alerts that have
- a printable payload data
- that have the following string: uid=0(root)
payload_printable:"uid=0\(root\)"You should enter it like this in Kibana:
Well what do you know - we got what we were looking for:
Some more useful reading on the Lucene Query Syntax (you should at least have a look :) ):
http://www.elasticsearch.org/guide/en/elasticsearch/reference/current/query-dsl-query-string-query.html
http://www.solrtutorial.com/solr-query-syntax.html
http://lucene.apache.org/core/2_9_4/queryparsersyntax.html